Until now, modern cryptography has consisted of asymmetric-key and symmetric-key algorithms.
ATOFIA Variable-Length encryption represents an innovative branch of cryptography that leverages Proof of Work and the principles of entropy. The scheme neither generates nor employs cryptographic keys.
A New Way to Secure the Future
Symmetric Key Cryptography
- AES-128, AES-256
- Twofish
- RC4
- Triple DES
Asymmetric Key Cryptography
- RSA
- Elliptic Curve
- ElGamal
Keyless Cryptography
- ATOFIA Variable-Length Encryption
Binary
Dynamic. Adaptive. Intelligent
ATOFIA Keyless Cryptography protects organizations from the attacks of today and the problems of tomorrow.
Binary
Our transformation routines transform every plaintext input into a final ciphertext output of binary numbers.
NO KEYS
Our advancements eliminate the need for the generation, distribution, and management of public and private keys.
NON-REPUDiATION
The sender of the message cannot deny sending the message and the recipient cannot deny having received the message.
INCREASES ENTROPY
Entropy is increased due to the randomness and inconsistency of every output.
SELF-DEFENDING
Every single 1 and 0 is equipped with a unique, self-defending halting mechanism based on a one-time constraint.
Non-Interactive
Our cryptographic protocol is constructed as a non-interactive proof of work.
In August of 2019, the United States Department of Commerce, Bureau of Industry and Security formally classified the ATOFIA Variable-Length Encryption Software, Version 1.0 software product under Export Control Classification Number (“ECCN”) 5D992.c.
This determination was based upon the software qualifying for the Encryption Commodities, Software and Technology (ENC) license exception as a “Mass Market Encryption Item.” This Mass Market Encryption Item is authorized for export and re-export under Section 740.17(B)(3) of the Export Administration Regulations (EAR).

ATOFIA Variable-Length Encryption
ATOFIA Variable-Length Encryption delivers a new, multi-layered solution to encryption and data security, giving organizations complete control, transparency, and security of their plaintext data.
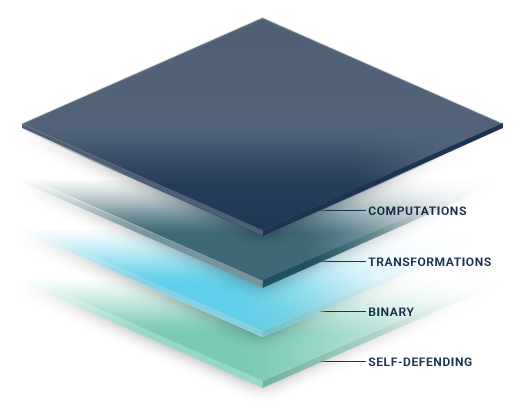
- Computations – Gödel's Incompleteness Theorems and modal ontological arguments are the foundation for our entropy-based models, generating incomplete and inconsistent outcomes for every output.
- Transformations – The encryption scheme includes three separate transformation states, with matrices dynamically changing at each level.
- Binary – Our transformation routines transform every plaintext input into a final ciphertext output of binary numbers.
- Self-Defending – Every single 1 and 0 is equipped with a unique, self-defending halting mechanism based on a one-time constraint.
We Welcome Your Questions and Comments.
With new technologies, there are always high levels of interest and curiosity. To learn more about the technology and the cryptographic functionality, drop us a line.
Simple. Distinct. Powerful.
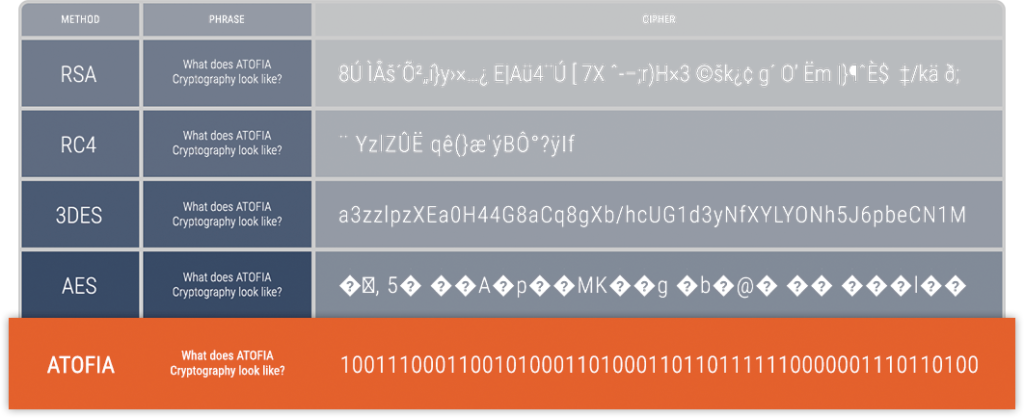
Today’s encryption solutions offer a variety of different ciphertexts. ATOFIA is delivering a new look and direction to ciphertext. Here’s how ATOFIA’s ciphertext compares to some of today’s most recognized: