Secure Your Intellectual Property

Take Your File Security to the Next Level
Decryption Rights
Only the authorized identities you select can decrypt and read your ATOFIA files.
Zero Trust
ATOFIA’s authentication server identifies and authenticates every user and device before access is granted to the application.
Team Sharing
You can encrypt any given plaintext file only once and every colleague in the recipient group can decrypt and read it independently of one another.
No Keys
Our advancements in keyless cryptography have led to the elimination of public and private key creation, distribution and management.
No Storage
With client side encryption, all your files reside locally on your device. ATOFIA cannot access, share, store, copy, decrypt, or read any of your files.
No Password
Your computer will automatically create a unique ATOFIA digital fingerprint for you and it will act as your electronic password. Your fingerprint is combinations of information about you and your computer.
Safeguard Your Intellectual Property Assets
$360+ BILLION
in annual losses in the United States from IP and trade secret theft.
1,000+
sensitive files are open to everyone in 53% of organizations.
$871,000
the average cost per credential theft incident.
Your IP Requires Rigorous Access Control
Each device and user is identified and verified before access is granted to the application. Gain complete control of which user and device can encrypt, share, and decrypt your valued data:
- Windows Desktop Application
- Self-Authentication
- No Off-Line Access
- Zero Trust Architecture
- Least Privileged Access
- Digital Fingerprint

Client-Side File Encryption
With client-side file encryption, your files are encrypted on your device before they are ever transmitted or shared.
You maintain complete control, ownership, and visibility over your encrypted files: where they travel, who can access them, and where they are stored.
Amazingly Easy to Use and Share
- Built-In ATOFIA Variable-Length Encryption
- One-Click Permissions
- Immutable Audit Log
- Share an encrypted file simultaneously with up to four recipients
- Transmit your encrypted file safely across insecured communication channels.
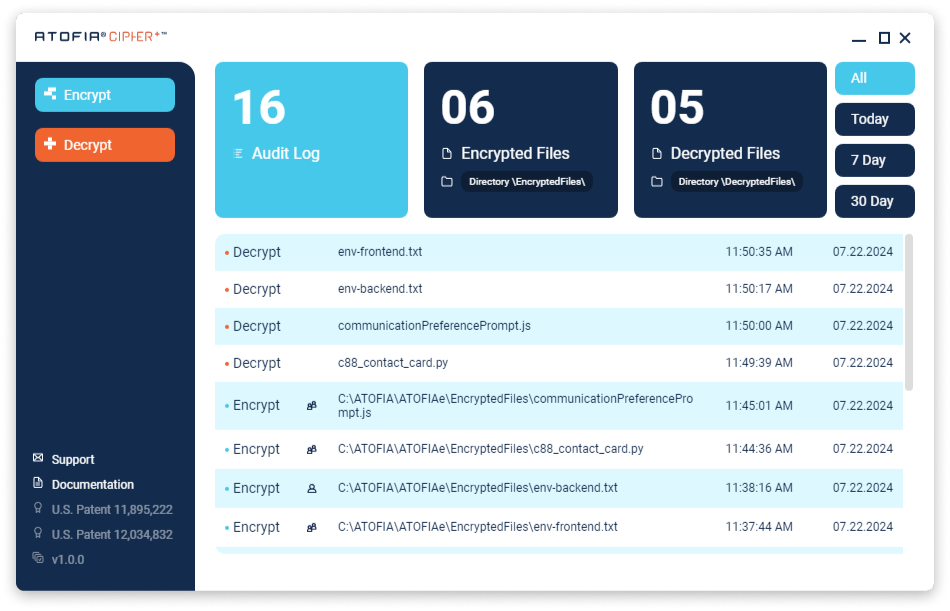
Secure Your IP and Business Secrets
Your innovation, value, and competitive edge is in constant motion across your day to day workflow. Whether you are in the C-Suite, HR, DevSecOPs, or anything in between, your most sensitive and business critical data is secured:
- Source Code
- Code Snippets
- Scripts
- Network Security Files
- API Keys
- 3rd Party API Keys
- Secret Keys
- Passwords
- Credentials
- Configuration Files
- Business Plans
- Supplier-Client Lists
- Employee Contracts
- Advertising Strategies
Reduce the Attack Surface
The application’s access control mechanisms, file policies, and encryption help safeguard your most valued IP and business secrets against cyber espionage and insider threats, attacks, and theft.
- Authentication: The identity of each machine and user is verified.
- Non-Repudiation: The proof of file origin cannot be denied.
- Data Integrity: The file is complete, intact, trusted, and has not been modified.
- Data Confidentiality: The file is encrypted and cannot be accessed by unauthorized parties during transmission or while at rest.
Protecting Your Innovation
150+
Support over 150 different plaintext file extensions.
333k
Encrypt files up to 333k in size.
8x
Smash bytes into bits.


